Security Policy
Keeping your data and your client’s information secure is our top priority.
Get peace of mind backed by our annual, third-party review of security systems
Data is secured by following the globally-recognized ISO 27001 standard
Every piece of data — from audio recordings to financial account information — is secured
Modern Security Architecture.
Our platforms and data are built and stored on two world-class systems: Microsoft Azure and Amazon AWS. All data is backed up across physical data centers and actively monitored by cybersecurity experts.


End-to-End Encryption.
Your data is encrypted in transit and at rest so it’s safe throughout the entire dictation process. All access is provisioned, logged, and monitored for ongoing protection.
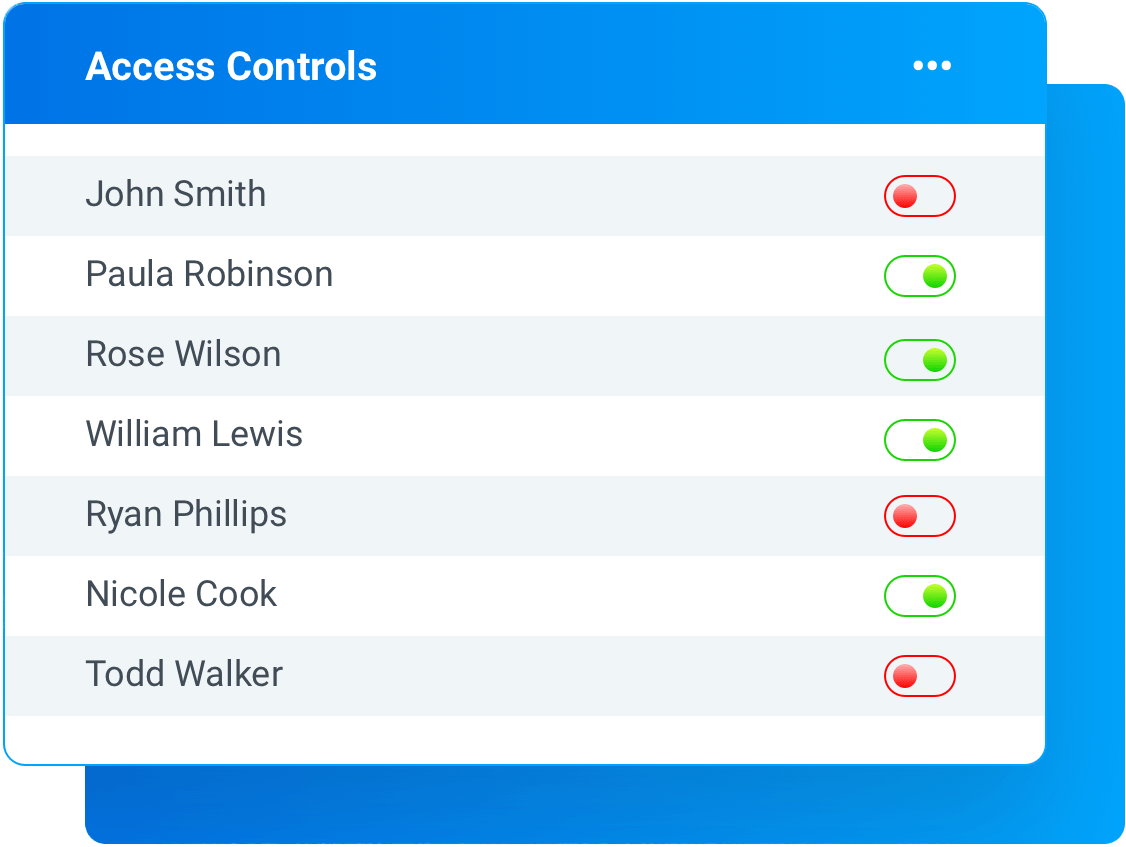
Complete Access Controls.
You control access within your team, and we control access with third-party integrations. All data is granted on a “need-to-know” basis and only provided as necessary.
“It’s not a stretch to say that advisors and their staff can achieve instant ROI with Mobile Assistant as a result of the efficiency and accuracy their service brings to capturing vital notes.”
Ready to Start?
Sign up for a free trial with the industry’s highest-rated dictation service.
Start a Free Trial
Create a free account to see how much time you can get back by speaking your notes.
Start Now
Explore Pricing
Whether you’re an enterprise with thousands of advisors or a solo RIA, we have plans that work for your needs and your budget.
See All Plans

